Cool Tricks:
Today I am going to tell you 2 almost less known and cool tricks, what can be used to break into someone’s system J ( Happy …. Haaaaaaaaa )
All these attacks are very simple, effective and their robustness lies that they exists in the main architecture of windows.
Trick 1:
The first one is API vulnerability. This is one of the most common security mistakes Developers always made (me too L ) while coding.
The syntax of CreateProcess API is:
BOOL WINAPI CreateProcess( __in_opt LPCTSTR lpApplicationName, __inout_opt LPTSTR lpCommandLine, __in_opt LPSECURITY_ATTRIBUTES lpProcessAttributes, __in_opt LPSECURITY_ATTRIBUTES lpThreadAttributes, __in BOOL bInheritHandles, __in DWORD dwCreationFlags, __in_opt LPVOID lpEnvironment, __in_opt LPCTSTR lpCurrentDirectory, __in LPSTARTUPINFO lpStartupInfo, __out LPPROCESS_INFORMATION lpProcessInformation);I am not going in deep and we are only interested in the first 2 parameters:
lpApplicationName and lpCommandLine.
The description of the API states as follow:
The lpApplicationName parameter can be NULL. In that case, the module name must be the first white space–delimited token in the lpCommandLine string.
So there are 2 ways to cal this API, firstly:
CreateProcess(_T("C://Windows//notepad.exe"),NULL …… )
And the second is:
CreateProcess(NULL,_T("C://Windows//notepad.exe"), …… )
The attack lies in these parameters only.
If we are using a long file name that contains a space, use quoted strings to indicate where the file name ends and the arguments begin; otherwise, the file name remain ambiguous for this API. For example, consider the string "c:\program files\sub dir\program name". This string can be interpreted in a number of ways. The system tries to interpret the possibilities in the following order:
c:\program.exe files\sub dir\program name
c:\program files\sub.exe dir\program name
c:\program files\sub dir\program.exe name
c:\program files\sub dir\program name.exe
and thus the main point to notice here is that while resolving path in that way if we put any of the malicious/hack program with above bold mentioned names ( ex: program.exe , sub.exe etc), that program will get launched in-spite of the targeted program.
Let’s have a practical look now.
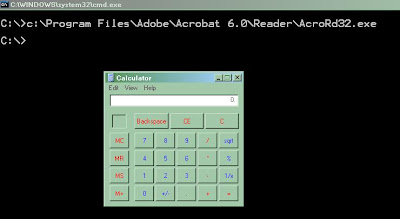
Copy “calc.exe” (calculator) or any other executable to C:\ and rename it to “Program.exe”
Now run the command prompt and type “Program files\\executbale.exe”
Like I have chosen:
C:\Program Files\Adobe\Acrobat 6.0\Reader\ AcroRd32.exe
Now type the whole path with “Quotes” and you can see Adobe reader gets launched as usual:
But then make a minor mistake (as most of the developers make while coding), only remove the quotes from this path and J :
BINGO!!!! In spite of Adobe reader, Calculator gets launched.
So the only thing you have to find out, is yours victim program calling any process and if yes try this attack on his/her executableJ . If successful, you have a way to launch your program with the credential of victims’ program and suppose if his program has got ADMIN privileges thenJ.
Trick 2:
This Hack also lies in the Windows Blind trusting of its registry entries.
Most of you might know about debuggers. A debugger or debugging tool is a computer program that is used to test and debug other programs , Microsoft provides a default debugger with Windows OS (Dr.WATSON) that gathers information about a program/computer system when an error (or user-mode fault) occurs with a program which helps them to figure out the main cause of the bug/crash.
A user can have more than one debugger in his/her system, In which scenario he/she has to decide that which one should be the default debugger of his/her system. I mean which debugger should invoke when any (remember ANY...) program on his/her system crashes.
The registry entry for this lies at:
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\AeDebug
You will find there a key with name: “Debugger”
And the value would be something like: "C:\WINDOWS\system32\vsjitdebugger.exe" -p %ld -e %ld
Now the hidden truth here is that Windows never checks that any executable mentioned there is actually a debugger or not, it simply launches it (I think by this time smile starts coming to your faceJ ), so just imagine an attack scenario where you change the victim’s registry entry with your tool path, you simply WAIT for some application to crash on your victims’ system (there are many, you need not worry, after every 10-15 minutes something will keep crashing)
As soon as your victims’ system crashes, Windows will launch your tool thinking it is a debugger and you are IN J (Yes need not even learn anything, let someone else’s’ mistake makes your way to your target system).
Enough theory (I hate this portion you know…), now just have some practical look (I love thisJ)
I wrote a very simple code which crashes every time we run it:
#include "stdafx.h"
#include "stdio.h"
#include "conio.h"
char *p;
void error()
{
p = NULL;
delete p;
}
int _tmain(int argc, _TCHAR* argv[])
{
p = new char(10);
error();
printf("%s",*p); //Error Trying to access invalid memory
// address
getche();
return 0;
Now run this code with the debugger registry's entry as:
"C:\WINDOWS\system32\vsjitdebugger.exe" -p %ld -e %ld
And yes as soon as the code crashes the VS debugger gets launched.
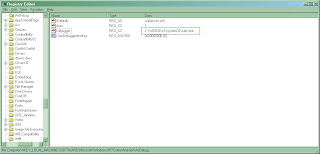
Now Change this registry entry with any dummy program name (in real world attack, this could be any MALICIOUS program)
Suppose I changed the entry with system calculator program path
“C:\WINDOWS\system32\calc.exe”
And run the same program again,
Now see the magic… BINGO!!!, The Calculator program gets launched, that too without coming in the knowledge of user as well as auto system provoked J